Blockchain technology has revolutionized various industries by introducing a decentralized and secure method of recording transactions. Alongside the well-known Proof of Work (PoW) and Proof of Stake (PoS) consensus models, the Proof of Authority (PoA) model has gained popularity in the realm of private blockchains. In this article, we will explore the definition, working principles, advantages, use cases, setup process, and challenges of Proof of Authority.
What is Proof-of-Authority? Understanding PoA Consensus Mechanisms
Proof of Authority (PoA) is a consensus method in blockchain networks where a specific group of validators is pre-selected as the governing authority. In this algorithm, trusted individuals or organizations choose nodes responsible for validating transactions and creating new blocks. Essentially, PoA ensures that only authorized entities have the right to validate transactions within the blockchain network.
This consensus system, Proof-of-Authority (PoA), relies on established validators to generate blocks, thereby enhancing the network’s computational power. Utilizing a Byzantine Fault Tolerance (BFT) algorithm, PoA enables comparatively faster transactions by leveraging identity as a stake in the process.
Proof of authority was first proposed in 2017 by Gavin Wood, co-founder of Ethereum blockchain and Parity Technologies. It was originally implemented on the POA Network, an Ethereum-based blockchain, before being adopted by other projects.

With proof of authority, transactions and blocks are validated by approved accounts known as validators. These validators run software that enables them to put transactions in blocks and add them to the blockchain.
The validators essentially act as moderators who are trusted to verify transactions honestly. Their reputation is at stake if they act maliciously.
Instead of stake or computational power, the validator’s identity serves as their stake in the network. This allows consensus to be achieved without the mining required in proof of work.
How Proof of Authority works?
Proof of Authority (PoA) is a consensus algorithm used in blockchain networks to validate and authenticate transactions. Unlike Proof of Work (PoW) and Proof of Stake (PoS), PoA relies on a limited number of trusted validators to confirm transactions and create new blocks.
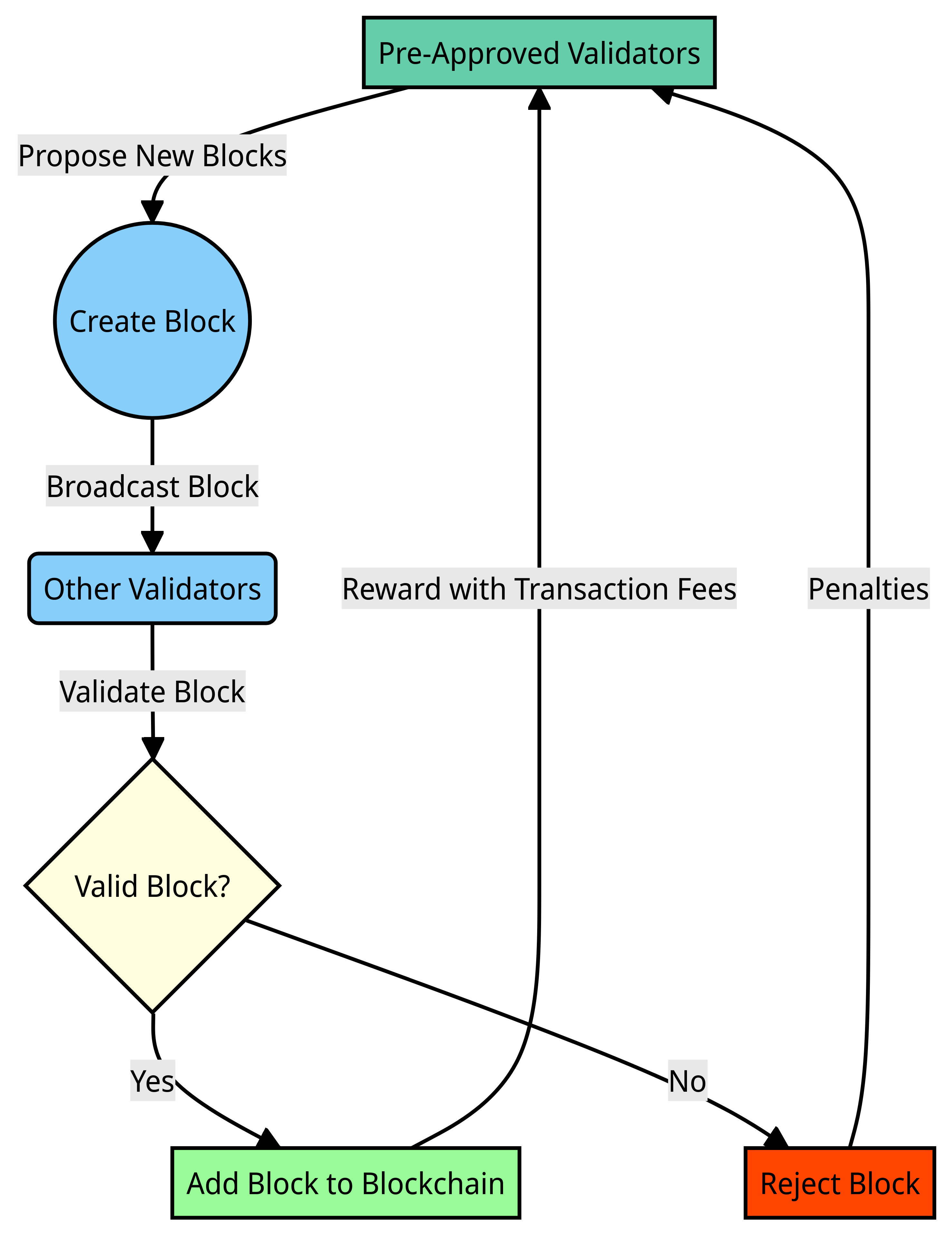
Here’s a detailed explanation of how Proof of Authority works:
1. Selection of Validators:
In a PoA system, a specific number of validators are chosen to participate in the network. These validators are typically known entities, individuals, or organizations with a proven track record of honesty and integrity. Unlike PoW, where miners compete to solve complex mathematical puzzles, or PoS, where validators are chosen based on the number of coins they hold, PoA validators are selected based on their identity and reputation within the network.
Validators need to register themselves in the public notary database using government-issued documents with the same identity that they have on the platform. Thus, blocks and transactions are verified by participants whose identities are already verified, serving as the authoritative figures within the system. This meticulous validation process ensures a higher level of security and integrity, making PoA networks resistant to compromise.
Because validators are pre-approved, the PoA mechanism is regarded ascentralized.
2. Transaction Validation:
When a transaction is initiated within the network, it is broadcast to all validators. The validators then verify the transaction based on predefined rules and the network’s protocol. If the transaction is valid, the validators reach a consensus and add the transaction to a new block.
3. Creation of New Blocks:
Validators take turns creating new blocks in the blockchain. The order of validators creating blocks can be predetermined or randomized, ensuring fairness. Each validator has the authority to create a block in a specified sequence. Once a validator creates a block and adds it to the blockchain, the other validators verify the block’s authenticity and, if valid, continue the consensus process for subsequent transactions.
4. Incentivization and Penalties:
Validators in PoA systems are typically incentivized for their participation. These incentives can be in the form of transaction fees or newly minted coins. The validators have a vested interest in upholding the network’s rules and validating transactions accurately, as their reputation and rewards are at stake. If a validator acts maliciously or tries to compromise the network’s integrity, there may be penalties, including the loss of rewards or exclusion from the validation process.
5. Security and Immutability:
PoA networks benefit from enhanced security due to the known identities of validators. This limited set of trusted entities significantly reduces the risk of attacks. Once a transaction is added to the blockchain, it is cryptographically secured and becomes immutable, meaning it cannot be altered or deleted. This immutability ensures the integrity of the blockchain and the transactions recorded on it.
6. Efficiency and Scalability:
PoA systems are highly efficient and scalable. The consensus process involving a limited number of validators results in faster transaction validations and high throughput. This efficiency makes PoA networks ideal for applications that require quick and seamless transactions, such as supply chain management, financial transactions, and identity verification processes.
7. Decentralization with Controlled Centralization:
While PoA involves a limited number of validators, it still maintains a degree of decentralization. The known identities and reputations of validators ensure a level of trust within the network. PoA strikes a balance between decentralization and efficiency, making it suitable for various use cases where a controlled level of centralization is acceptable.
In essence, Proof of Authority operates on the principle of trust and reputation. By relying on a select group of validators with established identities, PoA ensures the security, efficiency, and integrity of blockchain transactions, making it a popular choice for private and permissioned blockchain networks.
How are Validators Selected in a Proof of Authority Consensus System?
While anyone can participate in mining proof of work blockchains, validators must be approved to participate in a PoA network.
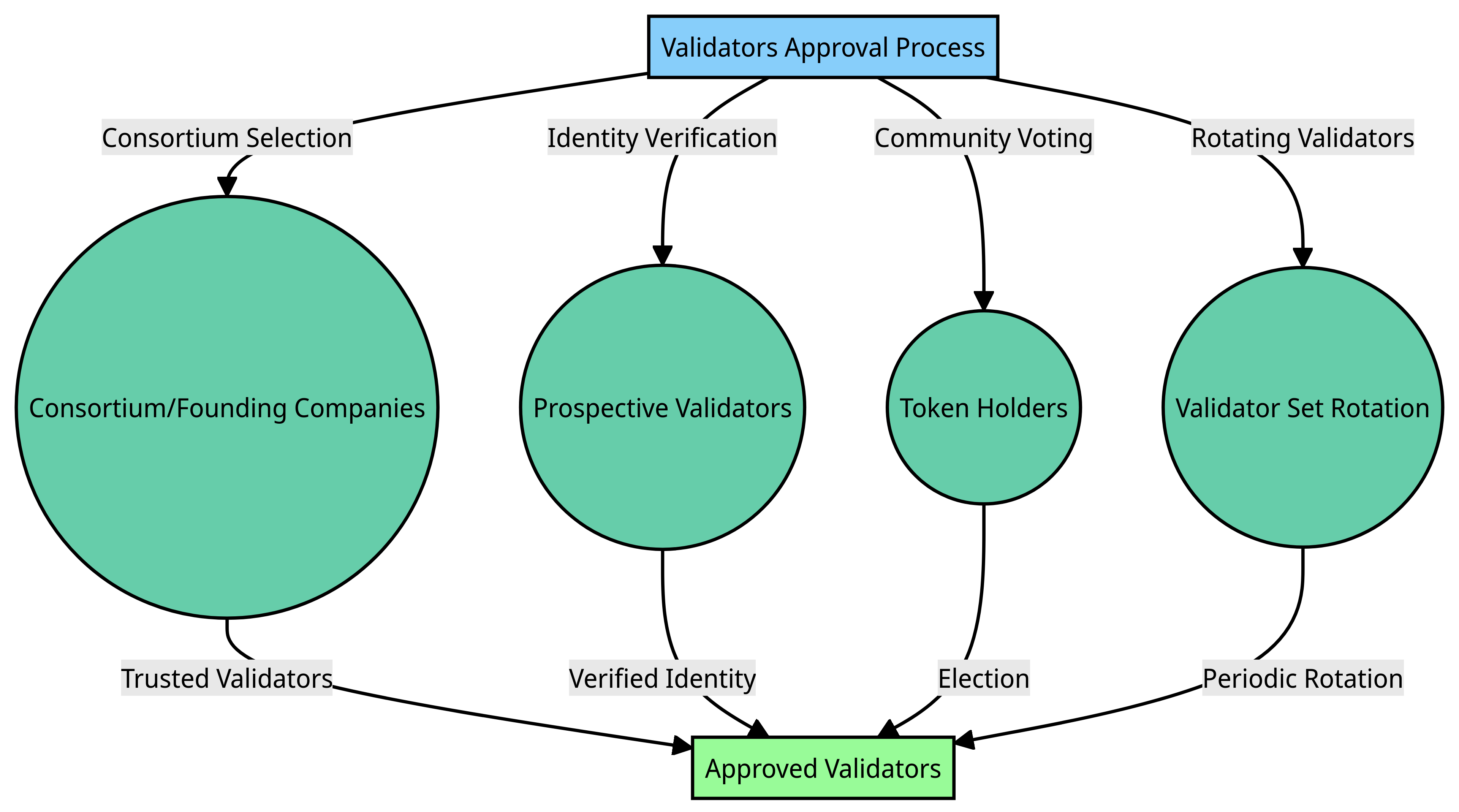
There are several methods used to select validators:
- Consortium selection – In private blockchains, the validators may be chosen by a consortium or group of founding companies running the network. Each company acts as a trusted validator.
- Identity verification – Prospective validators may need to verify their identity through documents and background checks. Their identity serves as their stake.
- Community voting – On some PoA networks, the community of token holders vote to elect validators from a pool of candidates.
- Rotating validators – The validator set can rotate on a periodic basis to allow different entities to participate in consensus.
Regardless of the selection method, the number of validators is kept relatively small compared to proof of work or proof of stake networks to enable faster consensus.
What are the Benefits of Proof of Authority?
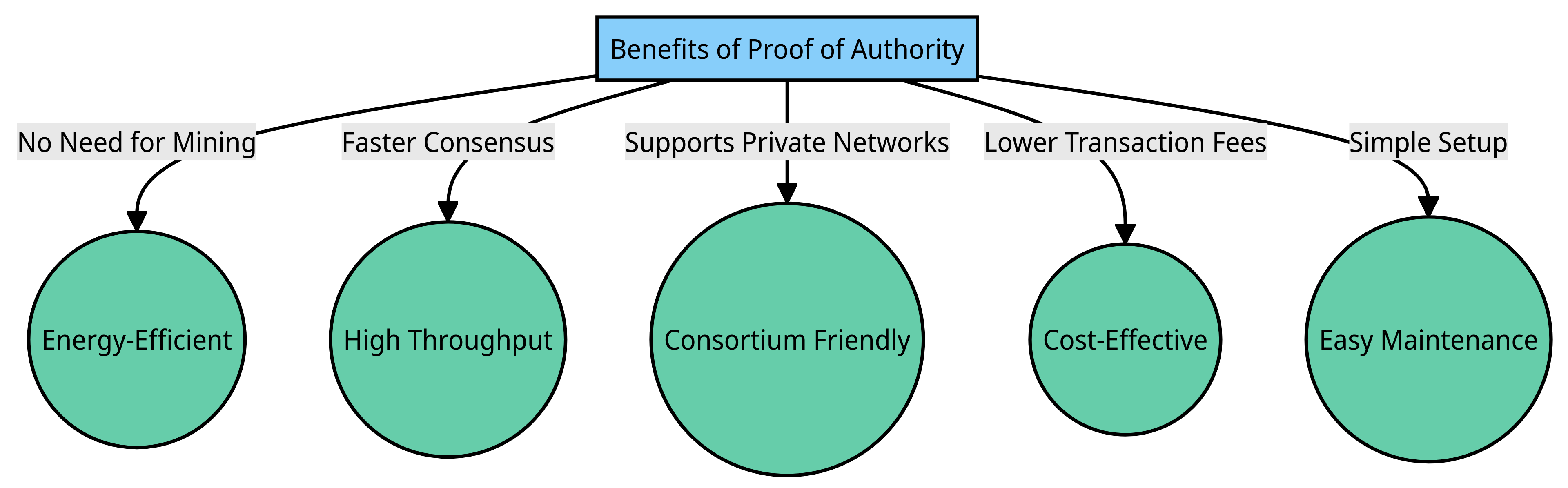
Proof of authority offers a number of advantages that make it well-suited for private or permissioned blockchains:
- No need for mining – PoA eliminates the energy-intensive mining required in proof of work, and the associated hardware costs. Transactions can be validated on low-cost consumer hardware.
- Faster consensus – With only a few trusted validators, PoA networks can validate transactions and blocks in seconds rather than minutes. This enables high throughput.
- Supports private networks – The ability to vet and approve validators fits better with private blockchain networks shared between a consortium.
- Lower transaction fees – Due to the efficiency gains, transaction costs can be kept relatively low compared to public blockchains.
- Simple setup – PoA networks are easier to set up and maintain with a limited number of trusted validators.
Proof of Authority (PoA) is a consensus algorithm employed in blockchain networks, where trusted individuals or organizations pre-select nodes responsible for validating transactions and creating new blocks. For these reasons, PoA is preferred for private networks where the validators are known to some degree. It sacrifices a degree of decentralization but offers faster performance. One of the main advantages of PoA over proof-of-work blockchains is the significantly reduced need for computing power, making it a more efficient and sustainable choice for certain applications.
What are Potential Use Cases for Proof of Authority?
Proof of authority is ideal for private or permissioned blockchains where the participants are trusted:
Enterprise blockchains – Shared between known partners, with each company operating a node. Improves speed and privacy over public networks.
Supply chain tracking – Allows supply chain partners to maintain a shared ledger for tracking goods.
Consortium blockchains – Enables groups of financial institutions or companies to run a joint blockchain network with known validator nodes.
IoT networks – Low cost method to achieve consensus among Internet of Things networks with verifiable devices.
Hybrid models – Can combine PoA consensus for private components alongside public blockchain transactions.
PoA also shows promise for enabling faster public blockchain networks if node validator identity mechanisms improve sufficiently in the future.
Real World Usage of Proof of Authority
Proof of Authority (PoA) is a consensus mechanism that relies on the reputation of a known set of validators to secure the network. PoA is often used in private and enterprise blockchains, where speed and scalability are more important than decentralization.
Here are some real-world examples of PoA in use:
- POA Network: POA Network is a public Ethereum-based blockchain that uses PoA with community-elected validators. POA Network is known for its fast transaction speeds and low fees.
- VeChain: The scalability of the proof-of-authority model is attributed to its reliance on a limited number of block validators. VeChain (VET) is a widely recognized platform that utilizes a Proof of Authority (PoA) algorithm.
- Hyperledger Fabric: Hyperledger Fabric is a popular enterprise blockchain framework that supports PoA as one of its pluggable consensus options. Hyperledger Fabric is used by many large companies, including IBM, Walmart, and Maersk.
- Private Ethereum networks: PoA is often used to achieve consensus among closed groups of validators running private Ethereum networks. Private Ethereum networks are used by businesses and organizations for a variety of purposes, such as supply chain management and asset tracking.
- Consortium networks: Consortium blockchains are permissioned blockchains that are governed by a group of companies or organizations. JPMorgan’s Quorum and R3’s Corda are two popular consortium blockchains that use variations of PoA.
PoA is still a relatively new consensus mechanism, but it is gaining traction in a variety of real-world applications. PoA is particularly well-suited for private and enterprise blockchains, where speed and scalability are more important than decentralization.
In addition to the examples above, PoA is also being explored for use in public blockchains. For example, the Ethereum Foundation is considering using PoA as a transitionary consensus mechanism as Ethereum moves to Proof of Stake.
What are Some Key Considerations with Proof of Authority?
While PoA offers significant benefits, it also has some drawbacks to consider:
- Centralization risks – Networks may trend toward centralization among a few powerful validators over time. Proper incentives are needed.
- Collusion potential – Pre-approved validators could potentially collude to alter transactions if they go rogue.
- Limited applications – May not be suitable for public networks without identity mechanisms to verify nodes.
- Overreliance on validators – Networks stand to suffer if a sufficient number of validators go offline.
- Regulatory uncertainty – The validator model and appointment process may come under regulatory scrutiny in some jurisdictions.
These risks can be minimized through decentralizing the validator selection process where possible, rotating validators routinely, and spreading distribution.
Proof of Authority vs. Proof of Stake and Proof of Work
Proof of Authority , Proof of Work and Proof of Stake are all consensus mechanisms used in blockchains to validate transactions and add new blocks to the chain. Each mechanism has its own advantages and disadvantages.
Proof of Authority
In a PoA blockchain, a limited number of pre-selected validators are responsible for validating transactions and adding new blocks to the chain. Validators are typically chosen based on their reputation, technical expertise, and financial stake in the network.
Once a validator is selected, they are given the authority to validate transactions and add new blocks to the chain. Validators are rewarded for their work with tokens or other incentives.
Some examples of PoA blockchains include:
- Hyperledger Fabric
- Quorum
- R3 Corda
Proof of Stake
In a PoS blockchain, validators are chosen based on their stake in the network. The more tokens a validator has staked, the more likely they are to be selected to validate transactions and add new blocks to the chain.
Validators in a PoS blockchain are rewarded for their work with tokens or other incentives. They are also penalized for malicious behavior, such as trying to validate invalid transactions or add new blocks to the chain that are not consistent with the rest of the blockchain.
Some examples of PoS blockchains include:
- Cardano
- Ethereum 2.0
- Solana
Proof of Work
In a PoW blockchain, miners compete to solve complex mathematical problems in order to earn the right to validate transactions and add new blocks to the chain. The first miner to solve the problem is rewarded with tokens or other incentives.
PoW is a very energy-intensive consensus mechanism, but it is also very secure. It is difficult for malicious actors to attack a PoW blockchain because they would need to control a majority of the mining power.
Some examples of PoW blockchains include:
- Bitcoin
- Litecoin
- Ethereum (currently)
Comparison of PoA, PoW and PoS
The following table summarizes the key differences between PoA, PoW and PoS:
| Characteristic | PoA | PoW | PoS |
|---|---|---|---|
| Validators | Pre-selected and authorized | Compete to solve mathematical problems | Elected by the network |
| Rewards | Tokens or other incentives | Tokens or other incentives | Tokens or other incentives |
| Energy efficiency | More energy-efficient than PoW | Less energy-efficient than PoA or PoS | More energy-efficient than PoW |
| Scalability | More scalable than PoW | Less scalable than PoA or PoS | More scalable than PoW |
| Security | More secure than PoW | Very secure | More secure than PoW |
| Centralization | More centralized than PoS or PoW | Less centralized than PoA or PoS | More centralized than PoW but less centralized than PoA |
In the PoA consensus algorithm, network nodes are pre-authenticated, allowing block generation rights to be granted only to nodes capable of withstanding DoS attacks. Consequently, the PoA network exhibits a superior resistance against attacks in comparison to PoS or PoW consensus mechanisms. This heightened security is attributed to the fact that even if a user managed to acquire 51% of the processing power, they would still be unable to compromise the network’s integrity.
Future of Proof of Authority
PoA is a promising consensus mechanism with a number of advantages, including:
- Speed: PoA blockchains are typically much faster than Proof of Work (PoW) blockchains, such as Bitcoin.
- Scalability: PoA blockchains can scale to handle a higher volume of transactions than PoW blockchains.
- Energy efficiency: PoA blockchains are much more energy-efficient than PoW blockchains.
- Security: PoA blockchains can be very secure, especially when used in private and enterprise settings with a known set of validators.
However, PoA also has some disadvantages, including:
- Centralization: PoA blockchains are less decentralized than PoW blockchains, as they rely on a known set of validators.
- Sybil attacks: PoA blockchains are more vulnerable to Sybil attacks, where an attacker attempts to gain control of the network by creating multiple identities.
Overall, PoA is a promising consensus mechanism with a number of advantages and disadvantages. It is particularly well-suited for private and enterprise blockchains, but it is also being explored for use in public blockchains.
Conclusion
Proof of authority offers a fast and efficient alternative to consensus for private or consortium blockchains where the validators are known and trusted. While it does sacrifice a degree of decentralization, it enables blockchains that are much cheaper to run and can process transactions far faster.
By harnessing the unique advantages of having approved validators, proof of authority carves out an important niche for blockchain adoption among enterprises. It provides a compelling model for running both private ledger systems shared between partners as well as public blockchain networks with verified identities.
There is no perfect consensus mechanism as each one has pros and cons. Though decentralization is seen as an advantage by the cryptocurrency community, PoA sacrifices decentralization to achieve high output and scalability.







