Introduction
Byzatine General’s Problem
The interesting concept of Byzantine Fault Tolerance (BFT) finds its roots in the renowned Byzantine General’s Problem, an appealing intellectual exercise that delves into the realm of logic. In this thought experiment, a group of respected generals is faced with the difficult challenge of planning a synchronized attack on a fortified city.
- The generals are scattered across the country and can only exchange messages one at a time via messenger.
- They must all coordinate the same action in order to successfully attack or withdraw.
- If they all go in for the kill, nobody will get hurt. If they can all just go away, they should be safe.
- When some generals advance while others pull back, it leads to a losing situation for everyone.
- The twist is that certain generals are disloyal and will try to confuse the other generals.
In the realm of military strategy, a perplexing challenge arises: how can a group of generals reach a unanimous consensus amidst the ever-present threat of treachery and deceit? This intricate predicament demands a solution that ensures cohesive decision-making, even in the midst of potential betrayal.
What is Byzatine fault tolerance (BFT)?
Blockchain platforms like Hyperledger Fabric, Zilliqa, and Tendermint have adopted the practical Byzantine Fault Tolerance (pBFT) consensus algorithm.
Hyperledger Fabric uses a variant of pBFT, following a permissioned approach. In contrast, Zilliqa employs a hybrid strategy, combining Proof of Work (PoW) and pBFT mechanisms to achieve consensus among network participants. These distinct consensus methods shape each platform’s unique characteristics and functionalities, establishing them as significant players in the evolving blockchain landscape.
Tendermint, a cutting-edge technology, utilizes both delegated Proof-of-Stake (PoS) and practical Byzantine Fault Tolerance (pBFT) consensus algorithms.
In a groundbreaking article titled “The Byzantine Generals Problem,” published in 1982, regarded researchers Leslie Lamport, Robert Shostak, and Marshall Pease presented a novel concept known as BFT (Byzantine Fault Tolerance). This revolutionary idea has since become an important foundation in the field of computer science.
Byzantine fault tolerance (BFT) refers to the remarkable capability of decentralized permissionless systems to detect and discard erroneous information. In the realm of decentralized systems, the concept of Byzantine fault tolerance holds great significance. A system is deemed Byzantine fault-tolerant when it successfully overcomes the Byzantine Generals’ Problem, a complex challenge that Bitcoin ultimately resolved through a distributed approach.
In the current state of affairs, individuals have the opportunity to participate in a decentralized and permissionless system, enabling them to freely share information. In the absence of Byzantine fault tolerance, the vulnerability of this system becomes apparent as a network member gains the ability to introduce false information, thereby risking the overall reliability of the network. Byzantine fault tolerance has emerged as a crucial concept in the realm of computer science. Its significance cannot be overstated, as it addresses a fundamental challenge in distributed systems.
How does Byzatine fault tolerance (BFT) apply to blockchain?
A blockchain is a decentralized system that can handle this issue without the need for a reliable central authority. Its node network resembles the generals in the previously mentioned game theory problem. They need to come to an agreement in order for the network to function properly, but they lack a reliable central entity to assist them in securely communicating with one another. Since all nodes need to decide on the same course of action and carry it out simultaneously, the same problem arises.
When Satoshi Nakamoto released the Bitcoin whitepaper in October 2008, he proposed a solution to the Byzantine Generals’ Problem. The proof-of-work (PoW) consensus process provided the answer. In this case, if a block contains a legitimate proof-of-work, represented by a hash, other network participants consider it valid. With this declaration, a mining node can add the block to the chain, indicating that all nodes in the blockchain’s network have come to an agreement. On the Bitcoin blockchain, transaction data is kept in blocks.
A block’s proof of work is provided by the PoW hash. This effort is represented by the money that Bitcoin miners spend on equipment and electricity to run their mining operations and create blocks. They are thereby deterred from behaving maliciously against the network by this investment. The Bitcoin blockchain is extremely reliable and safe because of the expensive mining process.
Other blockchains use various consensus algorithms to resolve the Byzantine Generals’ Problem. On the Ethereum blockchain, for example, proof-of-stake (PoS) is used to discourage network participants from acting against the network by requiring them to stake 32 ETH or less, depending on the staking mechanism they choose. If a stakeholder acts dishonestly, they risk losing their entire stake.
An example of how Byzatine fault tolerance works
It’s called a Byzantine fault in digital systems when a signal isn’t sure what it is, like a clear “0” or “1.” Think of it as a light switch that won’t go all the way off or all the way on.
In digital electronics, even a small amount of uncertainty can cause a lot of trouble. This uncertainty is a problem. It’s like having a light switch that flickers quickly, making it hard to see if the light is on or off.
We can solve this problem, though, by making sure that if there’s some doubt in the input, it doesn’t affect the end result too much, especially if there’s a clear and strong majority vote.
There are three people in a voting system, and they are deciding on something. We can be sure to say what the majority wants if three people agree and one isn’t sure (like the “1/2” signal).
Similarly, in a digital circuit, we can still get a clear and reliable output even if some parts aren’t sure what they want (like the “1/2” signal). This is because most of the parts are sure of what they want.
Practical Byzatine fault tolerance (pBFT)
Practical Byzantine Fault Tolerance (pBFT) is an innovative consensus algorithm designed to address the challenge of tolerating Byzantine faults, which refer to failures in nodes within a distributed system. By leveraging an effective and practical approach, pBFT aims to ensure the reliability and integrity of distributed systems, even in the presence of potentially malicious or faulty nodes.
This algorithm represents a significant advancement in the field of fault tolerance, offering promising solutions for enhancing the durability and trustworthiness of distributed systems. In a groundbreaking academic paper titled “Practical Byzantine Fault Tolerance,” Barbara Liskov and Miguel Castro unveiled a revolutionary concept in 1999.
The pBFT algorithm represents a significant advancement in the field of Byzantine fault-tolerant (BFT) systems, building upon the foundations laid by previous versions. In this model, it is assumed that there are independent node failures present. In addition, this assumption suggests that autonomous nodes have the potential to spread inaccurate or misleading information.
How does pBFT work?
In the pBFT consensus algorithm, nodes are required to provide evidence that a message originated from a particular peer node. In the realm of algorithms, there exists a set of rules that govern their operations. One such rule requires that nodes, which are essential components of these algorithms, must undertake the responsibility of verifying the integrity of transmitted messages.
This verification process ensures that the message remains unaltered throughout its journey. pBFT, or Practical Byzantine Fault Tolerance, operates under the basic idea that the presence of malicious nodes within a network must not exceed one-third of the total number of nodes. In the realm of complex systems, the probability of a scenario emerging wherein one-third of the nodes within the system exhibit malicious behavior reduces significantly from a mathematical standpoint.
In the realm of distributed systems, a cutting-edge technology known as a pBFT-based system has emerged. This system operates with a single primary node, which is often referred to as the leader node. The remaining nodes in the network serve as secondary or backup nodes. In this remarkable system, it has been discovered that any node has the potential to transform into a primary node.
In the event of a primary node failure, the system employs a backup mechanism wherein a secondary node effortlessly moves into the role of a primary node. In each round of the pBFT consensus algorithm, the primary node undergoes a change. In a fascinating display of decentralized decision-making, a significant number of trustworthy nodes within a network have the power to collectively oust a malfunctioning primary node.
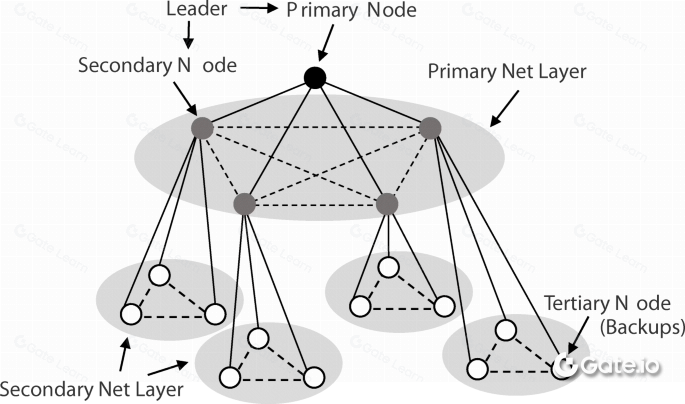
This democratic process involves replacing the problematic node with the subsequent node in the sequence, ensuring the network’s continued integrity and functionality.
- The leader node receives a request from a client.
- The primary node distributes the message to the secondary nodes.
- Both primary and secondary nodes carry out the execution of the client request. Subsequently, a response is dispatched to the client.
- The request can be deemed successful when the client receives “m+1” responses, with “m” representing the maximum allowable number of problematic nodes.
Blockchain platforms such as Hyperledger Fabric, Zilliqa, and Tendermint have embraced the utilization of the practical Byzantine Fault Tolerance (pBFT) consensus algorithm.
In the realm of blockchain technology, Hyperledger Fabric and Zilliqa stand out as two prominent platforms with distinct consensus mechanisms. Hyperledger Fabric, known for its permissioned approach, employs a variant of the Practical Byzantine Fault Tolerance (pBFT) consensus algorithm.On the other hand, Zilliqa takes a hybrid approach, combining both Proof of Work (PoW) and pBFT consensus mechanisms to achieve consensus among its network participants.
These differing consensus mechanisms contribute to the unique characteristics and functionalities of each platform, making them noteworthy players in the ever-evolving blockchain landscape. Tendermint, a cutting-edge blockchain technology, leverages the power of delegated Proof-of-Stake (PoS) and practical Byzantine Fault Tolerance (pBFT) consensus algorithms.
Advantages
The Practical Byzantine Fault Tolerance (pBFT) consensus algorithm possesses several advantages in comparison to other consensus algorithms, specifically the Proof of Work (PoW) approach. The mentioned benefits encompass the following:
- Transaction finality: The pBFT model makes transactions complete without the need for confirmations. If all the nodes agree that a suggested block is valid, then all the transactions in that block are sealed. In Proof of Work, each node checks a message on its own before a mining node adds it to the chain. It can take anywhere from 10 to 60 minutes for Bitcoin confirmations, depending on how many nodes are confirming the block.
- Low energy use: pBFT doesn’t need nodes to solve complicated math problems like PoW does, so it doesn’t use a lot of energy. Bitcoin miners need energy to do proof-of-work, which can cause them to use a lot of electricity.
- Even payouts: In pBFT, all nodes carry out the client’s request, which means that each of them gets paid.
Limitation
The ongoing communication required between nodes limits the scalability of pBFT-based blockchains. In the realm of network dynamics, it has been observed that networks possessing a multitude of interconnected nodes exhibit a notable delay in their ability to promptly address a client’s request.
In addition, it has been observed that blockchains utilizing the practical Byzantine fault tolerance mechanism are vulnerable to Sybil attacks. In a fascinating display of technological prowess, a nefarious technique known as a “Sybil attack” has emerged, captivating the attention of cybersecurity experts. This insidious maneuver involves a solitary entity taking command over a multitude of nodes within a network, thereby causing an interruption in the delicate balance of consensus. Recent research suggests that as the number of nodes in a network increases, the occurrence of Sybil attacks becomes increasingly unlikely.
In the realm of blockchain technology, the pBFT (Practical Byzantine Fault Tolerance) model has attracted attention for its durability in ensuring consensus among distributed nodes. However, as with any innovation, challenges arise. Scaling, in particular, has emerged as a significant concern for the pBFT model. To address this issue, developers have attempted to incorporate alternative consensus mechanisms alongside pBFT. A notable example is the Zilliqa project, which has adopted a hybrid approach to tackle scalability hurdles. By combining pBFT with other mechanisms, Zilliqa aims to enhance the efficiency and effectiveness of its blockchain network.
Variations of Byzantine fault tolerance
The consensus method that the creators chose determines the Byzantine fault tolerance that a blockchain exhibits. It should be noted that the level of Byzantine fault tolerance can vary among different blockchains.
Several widely used consensus algorithms include:
- Proof-of-work
- Proof-of-stake
- Delegated proof-of-stake (DPoS)
- practical Byzantine Fault Tolerance (pBFT)
- Leased proof-of-stake (LPoS)
- Proof-of-importance (PoI)
- Proof-of-authority (PoA)
- Direct Acyclic Graph (DAG)
- Delegated Byzantine Fault Tolerance (dBFT)
- Proof-of-capacity (PoC)
- Proof-of-identity (PoI)
- Proof-of-activity (PoA)
- Proof-of-elapsed-time (PoET)
FAQs
What exactly is a fault-tolerant Byzantine system?
A Byzantine fault tolerance system detects and rejects erroneous information through distributed nodes. It is also a system that can continue to function correctly even if certain nodes fail or provide misleading information. Through consensus methods such as proof-of-work and proof-of-stake, blockchain networks achieve Byzantine fault tolerance.
What is the significance of the name Byzantine fault tolerance?
Byzantine fault tolerance refers to a decentralized system’s capacity to continue operating reliably even if a few nodes act maliciously or fail. The name derives from the Byzantine Generals’ Problem in game theory. In this comparison, many Byzantine army units are positioned around a city with the intention of assaulting. Each division’s general relies on a messenger to communicate with one another. City defenses, on the other hand, may intercept the communication and alter or destroy it. The messenger might also misplace the message while it is in transit. Furthermore, rebellious generals could alter the message after successfully receiving it. As a result, these impediments may prevent the generals from launching an attack or retiring at the same moment.
What is the significance of the name Byzantine fault tolerance?
Byzantine fault tolerance refers to a decentralized system’s capacity to continue operating reliably even if a few nodes act maliciously or fail. The name derives from the Byzantine Generals’ Problem in game theory. In this comparison, many Byzantine army units are positioned around a city with the intention of assaulting. Each division’s general relies on a messenger to communicate with one another. City defenses, on the other hand, may intercept the communication and alter or destroy it. The messenger might also misplace the message while it is in transit. Furthermore, rebellious generals could alter the message after successfully receiving it. As a result, these impediments may prevent the generals from launching an attack or retiring at the same moment.
What exactly is the Byzantine process?
By solving the Byzantine Generals’ Problem, the Byzantine process attempts to make a system tolerant of failure. Blockchains do this by employing various consensus methods that prohibit nodes from acting maliciously in various ways.
Is Ethereum’s fault tolerance Byzantine?
Yes. To become Byzantine fault-tolerant, Ethereum employs the proof-of-stake consensus process. PoS requires stakers to lock 32 ETH or fewer—depending on the mechanism of staking—to avoid nefarious behavior against the network. Dishonest nodes or nodes that experience downtime on purpose may lose a portion or all of their staked ETH.
Is Bitcoin resistant to Byzantine faults?
Yes. To become Byzantine fault-tolerant, Bitcoin employs the proof-of-work consensus mechanism. A block cannot be declared valid by network nodes unless it contains a proof-of-work hash, which indicates that work was done to create it. Miners accomplish this through the bitcoin mining process, in which they invest a significant amount of money in hardware and electricity to generate new blocks. Because their money is on the line, miners are encouraged to act honestly.
What does Byzantine mean in blockchain?
Developers, like the Byzantine army generals in the analogy of the Byzantine Generals’ Problem, strive to design consensus mechanisms that force blockchain nodes to obey rules that make the network as tolerant as feasible to prevent failure. That is, a suitable consensus mechanism can let the network continue operating even if a few nodes are malfunctioning or purposefully propagating incorrect information.







